Design and Implementation of a Secure and Highly Available LAN

The goal of this project is to integrate top-tier technology, scalable to support company growth over 5-10 years,
while accommodating increased staff and new applications.
Improvements over the old network include VLAN segmentation for better bandwidth and performance,
centralized access point management, and dynamic IP allocation. To support an IoT-enabled smart building,
Additionally, a secure VPN for remote work and centralized equipment monitoring are essential to ensure efficient, user-friendly, and reliable network operations.
Here’s the Network Diagram we implemented
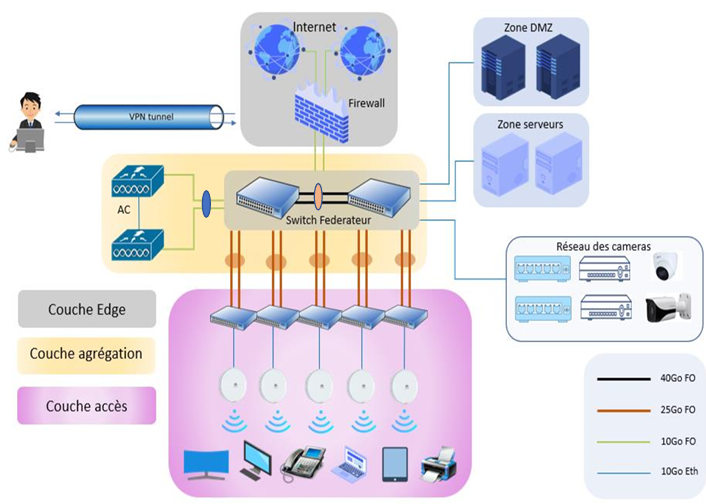
The network is mainly divided into three layers:
Edge layer
At the EDGE layer, we have integrated a firewall divided into two virtual systems,
with each system dedicated to one company, allowing for separate management of the two networks.
We have two WAN connections connected to our firewall:
the first connection provides 60 Mb/s reserved for TMI,
and the second connection provides 50 Mb/s reserved for ORADIST.
Agregation layer
The aggregation layer of our architecture consists of two core switches that connect all access switches,
as well as two highly available access controllers that enable centralized management of 33 access points
Access layer
The access layer of our architecture consists of access switches and access points.
The building has five floors, with one access switch and six access points on each floor.
The surveillance cameras are integrated into an independent network containing two NVRs connected by two access switches located in the ground floor and the basement.
Data transfer solution implemented
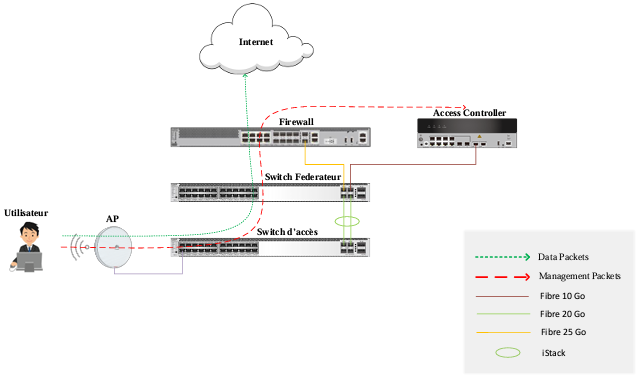
Management traffic is responsible for overseeing the entire network,
making it critical data that must be encrypted and encapsulated within a tunnel of the access controller.
However, local network data traffic is not encrypted. To prevent the controller from becoming a bottleneck and causing performance degradation in the network,
we have decided not to encapsulate data packets within the CAPWAP tunnel.
Access controllers
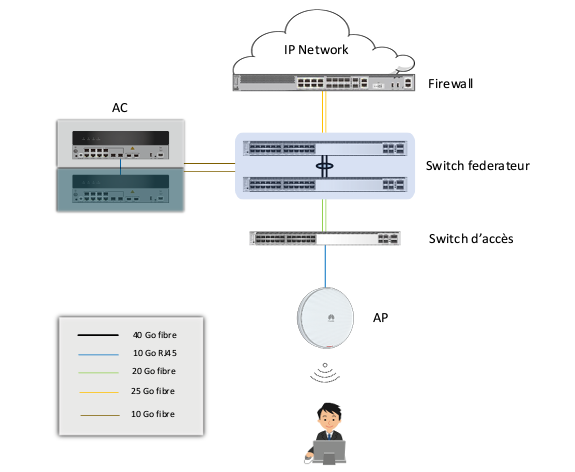
For the WLAN setup, we start by selecting the configuration mode for the controllers. In our case, we chose Bypass mode because:
- User traffic does not pass through the controller, which prevents overloading its resources.
- It supports scalability in the architecture, allowing us to add another controller or replace existing equipment without needing any changes to the overall architecture.
Availability Enhancement Mode
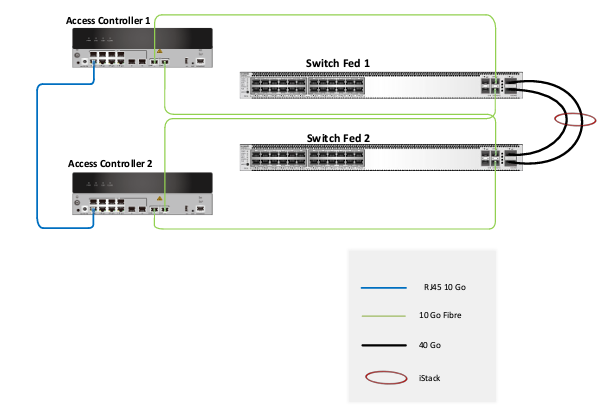
To ensure high availability in the Access Controllers (ACs), we used Active/Standby mode.
The decision to implement two controllers was made to guarantee high availability, creating a network that does not tolerate failures.
Link aggregation iStack
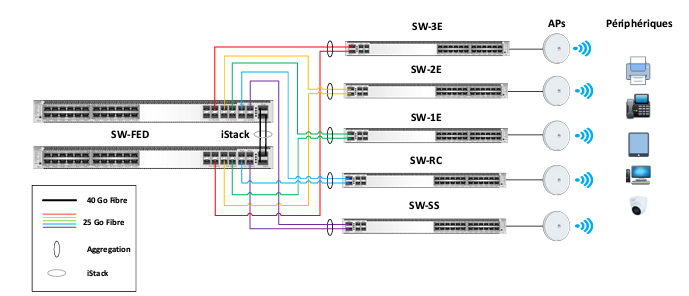
The core switches are deployed in iStack mode to achieve the following:
Two 24-port switches are stacked and operate as a single logical switch, creating a 48-port switch.
We used two 40 Gb/s QSFP links for the iStack configuration, ensuring redundancy and high performance with a total throughput of 80 Gb/s.
VPN solution
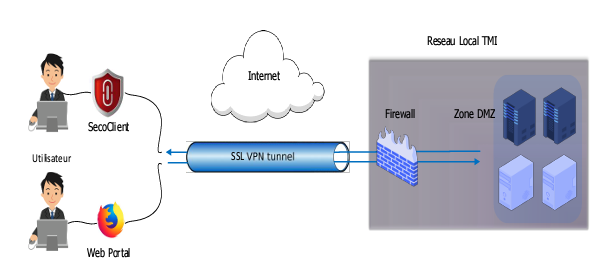
VPN access is available through the SecoClient application or via the web portal.
Users are imported from the authentication server.
Users are organized into groups.
To ensure security, each user is identified by their MAC address.
For each user group, we configured specific access rights to resources (servers and devices) to ensure security.
- Title: Design and Implementation of a Secure and Highly Available LAN
- Author: Malek ben jemia
- Created at : 2024-11-03 14:46:13
- Updated at : 2024-11-06 13:47:14
- Link: https://ma1ek.me/2024/11/03/Bachelor-Internship/
- License: This work is licensed under CC BY-NC-SA 4.0.
